There’s a hidden part of the internet that is much larger than the parts of the surface web you use every day – Facebook, Google, and Amazon. But do you really understand the information that is lying beyond those user-friendly and respectable websites? The Deep Web and the Dark Web, areas mostly used for hiding identities and sensitive data – usually for normal day-to-day housekeeping stuff. However the deeper you go, the more illegal and surprisingly awful and inhumane acts loom in much shadier, nearly invisible corners. But this vast ocean of content really isn’t invisible – you can access it – legally. But should you even want to visit the Deep or Dark Web?
In this session, we will discuss the definitions and realities of this portion of the web, as well as the topic of cryptocurrency/blockchain currency and the current trends in Bitcoin.
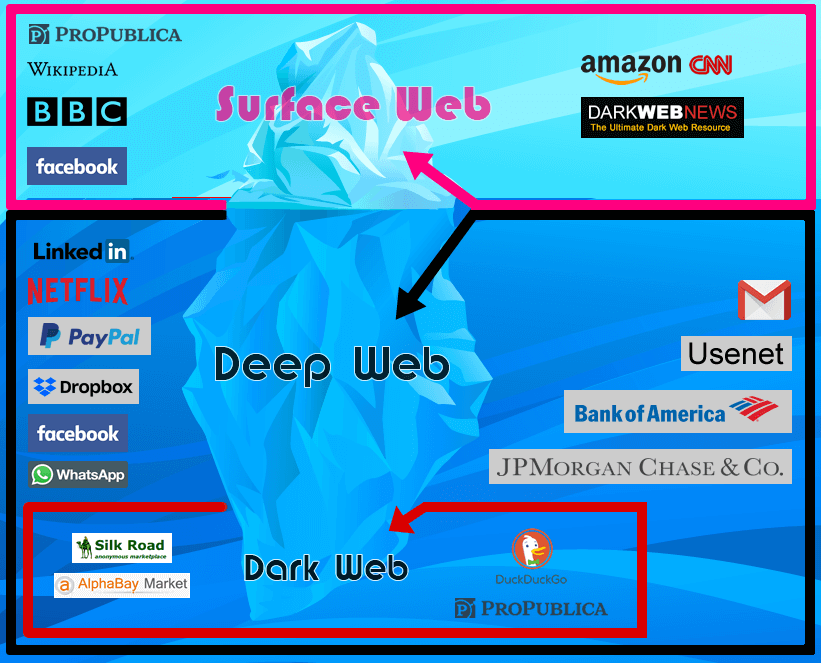
When you hop on your computer and go through the daily regiments of looking at the news, seeing who had a better dinner or night out than you on Facebook, Tweeting some nonsense about a cat or celebrity, posting selfies of your daily outfit on Instagram, bingeing on last night’s late night TV or catching up on The Bachelor, and buying dog sweaters on Amazon, you are utilizing what you might call the internet, but what is really known as the surface web. It is called this because it really is the top layer of a very large sea of information. The skin. The sunlight zone. The sod. This is where the easily accessed data lies. It’s rather safe (but obviously not really, given the amount of trouble that people can get in, or taken advantage of, or exploited…) and it’s easily accessible. You don’t have to try very hard to get the data or entertainment you need.
However, your presence is very well known. Each action you make – each link you click, each photo you look at, each tweet or IM you send, each search you initiate and every video you watch or song you listen to leaves a digital crumb. This crumb is essentially a trail you create, or story you involuntarily tell that is really available for anyone who really wants to know about can most likely follow or read. This is happening even with some of the most considered “safe” tech companies today: Google, Amazon, Apple, Microsoft, etc. Think of them as fishermen dipping a net into the sea as they cruise across the ocean surface. That is where all this information resides, and it is accessible to those who really want it. You never really sign off anywhere that your activity is private when you jump on to the internet. This is good news and bad news. If you behave well and are ethical, and use good judgement, then that is the trail that you leave. If your conduct online includes damaging or questionable behavior, then that is going to be part of your digital crumb or identity. Hope to run for office someday? Then somebody out there will find out about your Facebook posts of you drunk at Matt’s graduation, the friends of yours that are protesting a certain issue, the porn you have looked at and the juvenile goofy movies you and your BFFs made four years ago and posted on Youtube. We will get into this in more detail in the session on Digital Citizenship.
These trails or crumbs are something that many developers and programmers (and lots of bad people) wanted to eliminate right away in the early years of the internet. The Deep Web is an area where your identity and activity is more or less kept completely anonymous – mostly through encryption. Since the web works in a way that tracks and registers specific IP addresses and indexes, there are ways to participate and interact where those addresses and indexes, even databases, are hidden or removed – mostly by avoiding search engines and the method in which they discover and register pages found on servers.
From Wikipedia: (https://en.wikipedia.org/wiki/Deep_web)
Methods which prevent web pages from being indexed by traditional search engines may be categorized as one or more of the following:
- Contextual web: pages with content varying for different access contexts (e.g., ranges of client IP addresses or previous navigation sequence).
- Dynamic content: dynamic pages which are returned in response to a submitted query or accessed only through a form, especially if open-domain input elements (such as text fields) are used; such fields are hard to navigate without domain knowledge.
- Limited access content: sites that limit access to their pages in a technical way (e.g., using the Robots Exclusion Standard or CAPTCHAs, or no-store directive which prohibit search engines from browsing them and creating cached copies).
- Non-HTML/text content: textual content encoded in multimedia (image or video) files or specific file formats not handled by search engines.
- Private web: sites that require registration and login (password-protected resources).
- Scripted content: pages that are only accessible through links produced by JavaScript as well as content dynamically downloaded from Web servers via Flash or Ajax solutions.
- Software: certain content is intentionally hidden from the regular Internet, accessible only with special software, such as Tor, I2P, or other darknet software. For example, Tor allows users to access websites using the .onion server address anonymously, hiding their IP address.
- Unlinked content: pages which are not linked to by other pages, which may prevent web crawling programs from accessing the content. This content is referred to as pages without backlinks (also known as inlinks). Also, search engines do not always detect all backlinks from searched web pages.
- Web archives: Web archival services such as the Wayback Machine enable users to see archived versions of web pages across time, including websites which have become inaccessible, and are not indexed by search engines such as Google.
Basically, the Deep Web encompasses all encrypted data, users and activity – information that search engines can’t find or access. This includes all user databases, webmail pages, registration-required web forums, pages behind paywalls, and anything else that should never be seen by the general public. There are huge numbers of such pages, and most exist for mundane reasons – and that’s great.
The content management system (CMS) into which I am creating this session is on the Deep Web. As is how I create every page that is on the class site until I am ready to set it “live” – at which point it becomes a part of the traffic that web crawlers and search engines can mine and process so that access by the average web user is available. Meanwhile our university intranet – Moodle and Exchange is hidden from search engines, and requires a password.
Use an online bank account? The password-protected bits are on the Deep Web. And when you consider how many pages just one Gmail account will create, you understand the sheer size of the Deep Web. All things stored and shared on Google Drive are living in the Deep Web. If you use PayPal or Dropbox – you are using it. So most likely, most of you are taking advantage of the Deep Web on a daily basis. So you should see that it is not as bad as it sounds – so far.
WIRED Magazine has an interesting article about protecting yourself when browsing the web. Please Read.
The other side of the Deep Web encompasses a rather darker side of commerce and information delivery. This is known as the Dark Web. This area is more about actual websites, not data or personal info that is trying to be protected, like bank account info. Sites that might offer something that shouldn’t be seen on the surface web – and many, if not most, pursuing illegal operations. The worst stuff that is happening right now in so many of our cultures is taking place on the Dark Web: stolen goods, sex trafficking, child pornography, illegal drugs, slavery, murder and torture are only among the few. It’s the new black market and facility where criminals can conduct “business” and for the most part be hidden and “safe”.
 Almost all sites on the Dark Web hide their identity using the Tor encryption tool. Tor has the ability to hide your identity and activity. You can use Tor to generate a false location so it appears you’re in a different country, making it much harder to pinpoint where you as the user is actually computing from.
Almost all sites on the Dark Web hide their identity using the Tor encryption tool. Tor has the ability to hide your identity and activity. You can use Tor to generate a false location so it appears you’re in a different country, making it much harder to pinpoint where you as the user is actually computing from.
When a website is run through Tor it has much the same effect. To visit a site on the Dark Web that is using Tor encryption, the web user needs to be using Tor. Just as the end user’s IP address is bounced through several layers of encryption to appear to be at another IP address on the Tor network, so is that of the website.
There are several more layers of secrecy than the already secret act of using Tor to visit a website on the open internet – for both parties.Therefore, sites on the Dark Web can basically be visited by anyone, but it is very difficult to work out who is behind the sites. And it can be dangerous if you slip up and your identity is discovered.
Why would I want to use the Dark Web?
Not all Dark Web sites use Tor. Some use similar services such as I2P, for example the Silk Road Reloaded. But the principle remains the same. The visitor has to use the same encryption tool as the site and – crucially – know where to find the site, in order to type in the URL and visit.
Yes, too much of this resource is used for awful things, but there are also legitimate uses for the Dark Web.
People operating within closed, totalitarian societies can use the Dark Web to communicate with the outside world. And given recent revelations about US and other government snooping on web use, one might feel it is sensible to take your communication on to the Dark Web.
The Dark Web hit the headlines in August 2015 (and many times since) after it was reported that 10GB of data stolen from Ashley Madison, a site designed to enable bored spouses to cheat on their partners, was dumped on to the Dark Web. Hackers stole the data and threatened to upload it to the web if the site did not close down, and they eventually acted on that threat. Now the spouses of Ashley Madison users have received blackmail letters demanding they pay $2500 in Bitcoin or have the infidelity exposed.
Many national governments have launched dedicated cybercrime units to tackle the Dark Web, with a particular focus on cracking down on serious crime rings and child pornography, like The National Crime Agency.

ZYGOTE films made a documentary about the Deep & Dark web. This is your video assignment this week.
What is Cryptocurrency?
Cryptocurrency is a tough concept for some to wrap their brains around – me included! I think a lot of the confusion comes from our set paradigm on money. The value of the dollar, the distribution and minting of money, the regulation and taxation and laws surrounding exchange – it’s all presided over by a central, organized government. There’s also a physical nature to traditional currency; understanding my bank balance is just a value, I can go and make a withdrawal and have actual dollars in my hands. I can draw on that balance for something that I can hold.
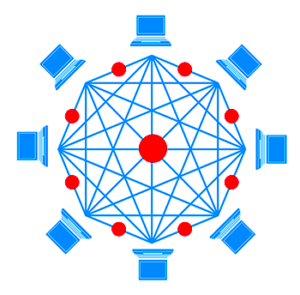
Cryptocurrency is different. It exists only digitally in a decentralized system of millions of computers in a peer-to-peer network that is intentionally designed to be impervious to fraud or theft.
 While numerous kinds of cryptocurrency exist, the most exchanged and highest valued example is Bitcoin. I will use Bitcoin as an example throughout this section, but I do want you to know they’re not the only platform making progress in this burgeoning arena. Click quickly over to this link for an idea of the numerous different cryptocurrencies and their drastic range of values: https://coinmarketcap.com/.
While numerous kinds of cryptocurrency exist, the most exchanged and highest valued example is Bitcoin. I will use Bitcoin as an example throughout this section, but I do want you to know they’re not the only platform making progress in this burgeoning arena. Click quickly over to this link for an idea of the numerous different cryptocurrencies and their drastic range of values: https://coinmarketcap.com/.
How does a decentralized cryptocurrency work? Blockchain
There are a few inherent challenges with a currency that only exists in the digital world. The first, and likely most important, is the guarantee and tracking of the 1:1 exchange. How can you know that the one Twiggcoin I just sent to you hasn’t been emailed out to a dozen other students? What if that Twiggcoin that I’m paying you wasn’t mine in the first place? How can I prevent programmers from replicating Twiggcoins to the point of obsolescence? Or keep hackers from stealing all of my Twiggcoins? Without a centralized ledger – like the US dollar or any government backed banking system – cryptocurrencies had to develop a system that was trustworthy and that could maintain value by guaranteeing ownership and a pro-rata transactional exchange of ownership.
 Coders – when using their powers for good – can achieve incredible things. The Blockchain is one of the most revolutionary new uses of technology that we have experienced in living memory. That’s a bold statement – I know – but stay with me.
Coders – when using their powers for good – can achieve incredible things. The Blockchain is one of the most revolutionary new uses of technology that we have experienced in living memory. That’s a bold statement – I know – but stay with me.
Blockchain is the platform that created cryptocurrencies’ shared ledgers. A currency’s ledger is an accounting of the quantity cap and ownership of every single portion of that currency. Through Blockchain, these exist on a network of hundreds of thousands of computers, providing that records of historic transactions are preserved in perpetuity, while building new an updated transactions onto the front of the chain. The decentralized nature of the Blockchain protect against some of the challenges I listed earlier. With multiple, identical copies of the ledger existing in unaffiliated locations, theft and fraud from the ledger become nearly impossible. The creation of new currency is also controlled, and pro-rata ownership transactions can be trusted. The decentralized system also provides for new opportunities, particularly in markets and uses that do not have the infrastructure of a more traditional, centralized system.
For those of you with Netflix, I am going to suggest – highly recommend – encourage mightily – but not require – that you watch the two-hour documentary, Banking on Bitcoin. There is a wealth of detailed history and information that will give you a far deeper understanding of cryptocurrency than this brief overview. This could very well be the money of the future, and the more familiar you are with it today, the better prepared you will be to be versatile in the changing landscape of digital tender.
Can I pay my tuition with Bitcoin?
Well, no. But you can sell your Bitcoin or other cryptocurrency for its value in US dollars through exchanges that accept it. You can also use cryptocurrency at some online vendors like NewEgg, Microsoft, and Overstock. There seems to be new speculation every week about how and when giants like Amazon and Walmart may get into the cryptocurrency arena. But how does a transaction work? This flowchart offers a good first, then, next of the process:
Are Bitcoin and other cryptocurrencies legit?
Good question. Cryptocurrencies truly only have value because there are enough people who think they do. Their speculative value is based purely on what people are willing to pay for them. Currency is only valuable if it has a use, and right now, Bitcoin and its colleagues have filled niches in positive and negative ways. As noted in Don Tapscott’s talk, the ability to digitally send funding across the world with only a pair of cell phones could create social mobility in ways we haven’t seen. Positive uses of these new ways to account for, create and track wealth are many. There is also room for concern about the lack of accountability with this kind of exchange. The Dark Web has unending opportunities to exploit and do harm to people, and cryptocurrency is currently funding all of them. It creates an anonymous stream of money for people whose only aim is to cause suffering in others. It’s something to consider while the legality of cryptocurrency, how it’s taxed, and what kind of regulations are possible.
In my mind, there are more questions right now than answers about the future of cryptocurrency, but one thing is certain. Whether any of its current models will be viable in the future, cryptocurrency is here to stay.
Rhett & Link from Good Mythical Morning do a great job of explaining Cryptocurrency. Please watch.
For another explanation and further examples of how these systems can help to transform economic conditions around the world, watch this TED Talk:
The IRS is a bit freaked by the power of Cryptocurrency. Read this NYTimes.com article to learn why.